Modern Departments of Corrections (DOCs) operate under a microscope, where every decision made by staff can be subject to intense legal and public scrutiny. When agencies rely on fragmented emails, unmanaged spreadsheets, or informal handoffs to manage their daily operations, they create significant vulnerabilities that can lead to disastrous outcomes during audits or investigations. To mitigate these risks, DOCs must focus on designing corrections workflows that hold up under scrutiny by building process integrity directly into their digital infrastructure. A defensible workflow is not merely a digital version of a paper process; it is a structured system where every action follows a strictly defined path, is performed only by an authorized role, and is automatically recorded in a way that cannot be manipulated. This level of structure moves beyond simple task management to support a culture of accountability and transparency that protects both the staff and the institution.
By shifting from ad hoc, manual processes to a structured digital model, correctional agencies ensure that their operations are fast and legally sound. This transformation is essential for meeting regulatory expectations and maintaining the confidence of external oversight bodies. The goal is to eliminate “he-said-she-said” scenarios by providing a single, immutable version of the truth that can be reconstructed months or even years after an event has occurred. When internal policies and external regulations are followed consistently every time, the agency’s process integrity evolves from a potential liability into a strategic advantage.
The Defensible Workflow Model
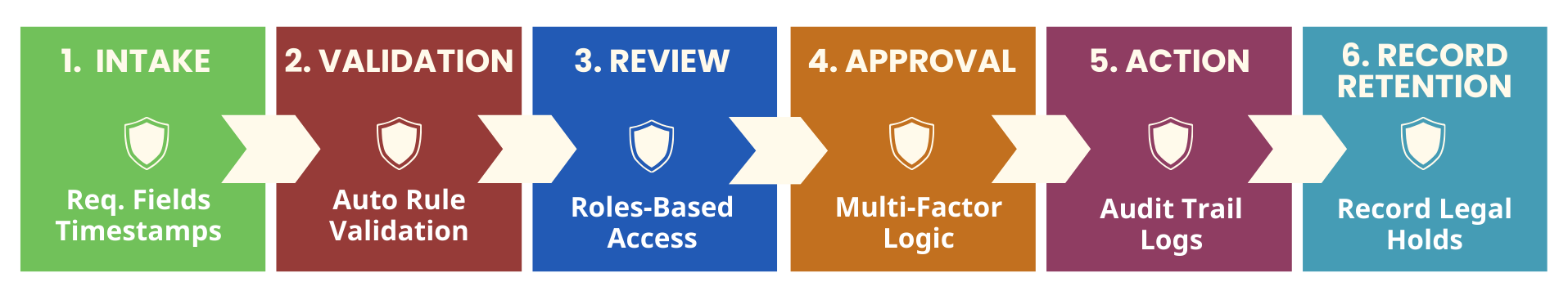
Resource Spotlight: To see a visual breakdown of how these phases interconnect to protect your agency, you can download the full Defensible Workflow Model PDF here to share with your compliance and IT leadership teams.
Phase One: Intake and the Foundation of Data Integrity
The journey toward a defensible system begins at the point of entry. In the defensible workflow model, the first stage is Intake. This is where information is captured and the digital trail begins. To ensure this phase holds up under scrutiny, the system must utilize required fields and automatic timestamps. Required fields prevent the common issue of incomplete documentation, ensuring that no record moves forward without the baseline data necessary for compliance.
Timestamps serve as the chronological backbone of the workflow. Because they are generated automatically by the system rather than entered manually by a user, they provide an indisputable record of when an action was initiated. This prevents retroactive data padding and ensures that the agency can prove exactly how long a process took, which is often a critical factor in legal challenges or internal investigations regarding response times and due process.
Phase Two: Automated Rule Validation
Once data has been captured, the next step in a high-integrity workflow is Validation. In many legacy systems, validation is a manual check performed by a supervisor, which is prone to human error or oversight. A defensible model replaces or augments this with Auto Rule Validation. By embedding the agency’s specific business rules and legal requirements directly into the software, the workflow can automatically detect inconsistencies or missing prerequisites.
This automated layer of oversight ensures that no step is bypassed or altered without proper authorization. For example, if a specific form requires a medical clearance before an inmate transfer can be approved, the system will prevent the workflow from advancing until that condition is met. This automated gatekeeping strengthens oversight and guarantees that internal policies are followed consistently every time, regardless of how busy the facility may be.
Phase Three: Review and Role-Based Access Control
As a document or task moves into the Review phase, the focus shifts to security and authorization. A defensible workflow must ensure that only the right people are looking at the right data at the right time. This is achieved through Role-Based Access Control (RBAC). Instead of broad access permissions that can lead to data leaks or unauthorized changes, RBAC limits interaction with the workflow based on the user’s specific job function and authority level.
This phase is critical for maintaining a chain of custody for digital information. When an auditor asks who reviewed a specific incident report, the system can provide a definitive answer backed by secure login credentials. Because the workflow is performed by an authorized role as defined by the system, it reinforces the legality of the process. This structure prevents unauthorized personnel from interfering with sensitive data, further protecting the agency from claims of procedural mishandling.
Phase Four: Approval and Multi-Factor Logic
The Approval stage is often the most scrutinized part of any correctional process. Whether it is a disciplinary action, a release authorization, or a high-level administrative change, the approval must be airtight. To achieve this, the model utilizes Multi-Factor Logic. This goes beyond a simple digital signature; it involves complex logic gates that may require multiple layers of approval or specific conditions to be met before a final sign-off is recognized by the system.
This multi-factor approach ensures that high-stakes decisions are not made in a vacuum or by a single individual without proper oversight. It creates a checks and balances system that is built into the digital fabric of the document. By enforcing these logical hurdles, the agency can demonstrate to investigators that every approval followed a rigorous, pre-defined path that was designed to prevent errors and ensure regulatory compliance.
Phase Five: Action and the Comprehensive Audit Trail
Once approval is granted, the workflow moves into Action. However, in a defensible model, the action itself is not the end of the story. Every action must be accompanied by audit trail logs. These logs record every interaction with the record: who viewed it, who edited it, what was changed, and when the change occurred. This level of detail provides a complete, 360-degree view of the process life cycle.
Audit trail logs are the primary defense against “he-said-she-said” scenarios. If a record is challenged in court, the agency can produce a log that shows an unbroken history of the document. This transparency provides confidence to stakeholders that the agency’s operations are being conducted with the highest level of integrity. It transforms the digital record into an immutable version of the truth that can withstand the most rigorous legal examination.
Phase Six: Record Retention and Legal Holds
The final stage of the model is Record Retention. In corrections, the duty to preserve records often extends for years or decades. A defensible workflow includes specific mechanisms for Record Legal Holds. When an investigation or lawsuit is pending, the system must be able to freeze relevant records to prevent them from being deleted or altered according to standard retention schedules.
This capability is vital for meeting legal discovery requirements. If an agency fails to produce records or if those records have been altered after a legal hold was supposed to be in place, it can lead to severe legal sanctions and a loss of public trust. By automating the retention and hold process, agencies ensure they remain in compliance with external regulations consistently, every time.
Why Process Integrity is a Strategic Advantage
Implementing these six stages allows Departments of Corrections to design workflows that align operational reality with strict regulatory expectations. The transition from fragmented, manual systems to a structured digital model does more than just speed up the work—it protects the agency. It ensures that every step of a process can be reconstructed after the fact, providing a clear narrative of what happened and why.
When an agency can prove its compliance through a defensible workflow, it reduces risk across the board. It strengthens the agency’s position during audits, provides clear evidence for internal investigations, and offers a robust defense against litigation. Ultimately, this leads to a more professional, transparent, and accountable organization that can focus on its core mission of public safety without the constant threat of procedural liability.